API Keys
An API key is a unique identifier to authenticate requests to an Application Programming Interface (API). It acts as a code that allows the API provider to track and control how the API is being used, ensuring that only authorized users can access the services. Cloud Orbiter provides authentication services that extend standardized and secure access using token-based authentication corresponding to the sessions maintained by Keycloak. This method is mainly suited for browser-based access, where the password used for authentication remains with the user. It is usually paired with two-factor authentication (2FA), providing another security layer.
However, in scenarios like integrating CI/CD pipelines or enabling another layer of custom logic or automation-provided services, consumers might want to have their business process in place. It adds to the need for auth microservices to provide another standardized API key-based authentication layer, enabling the secure triggering of REST APIs via CI/CD workflows and system integrations for secure device-to-device communication. Traditionally, API keys have been the most adopted industry-wide for such requirements.
The API key management need to have the following:
-
The system must provide the option to create, manage, list, delete, enable or disable multiple API keys. This capability allows for associating different API keys with different devices or consumers.
-
The system should allow the creation of API keys with an associated expiry time. It ensures the key automatically expires after the given time, facilitating hassle-free key management.
-
Maintain visibility of when any specific key was used the last time, indicating activity for the same.
API Key Management Solution by Cloud Orbiter
Cloud Orbiter provides API key management functionalities, ensuring a level of security such that keys are kept secure during their lifetime.
API Key Functionalities
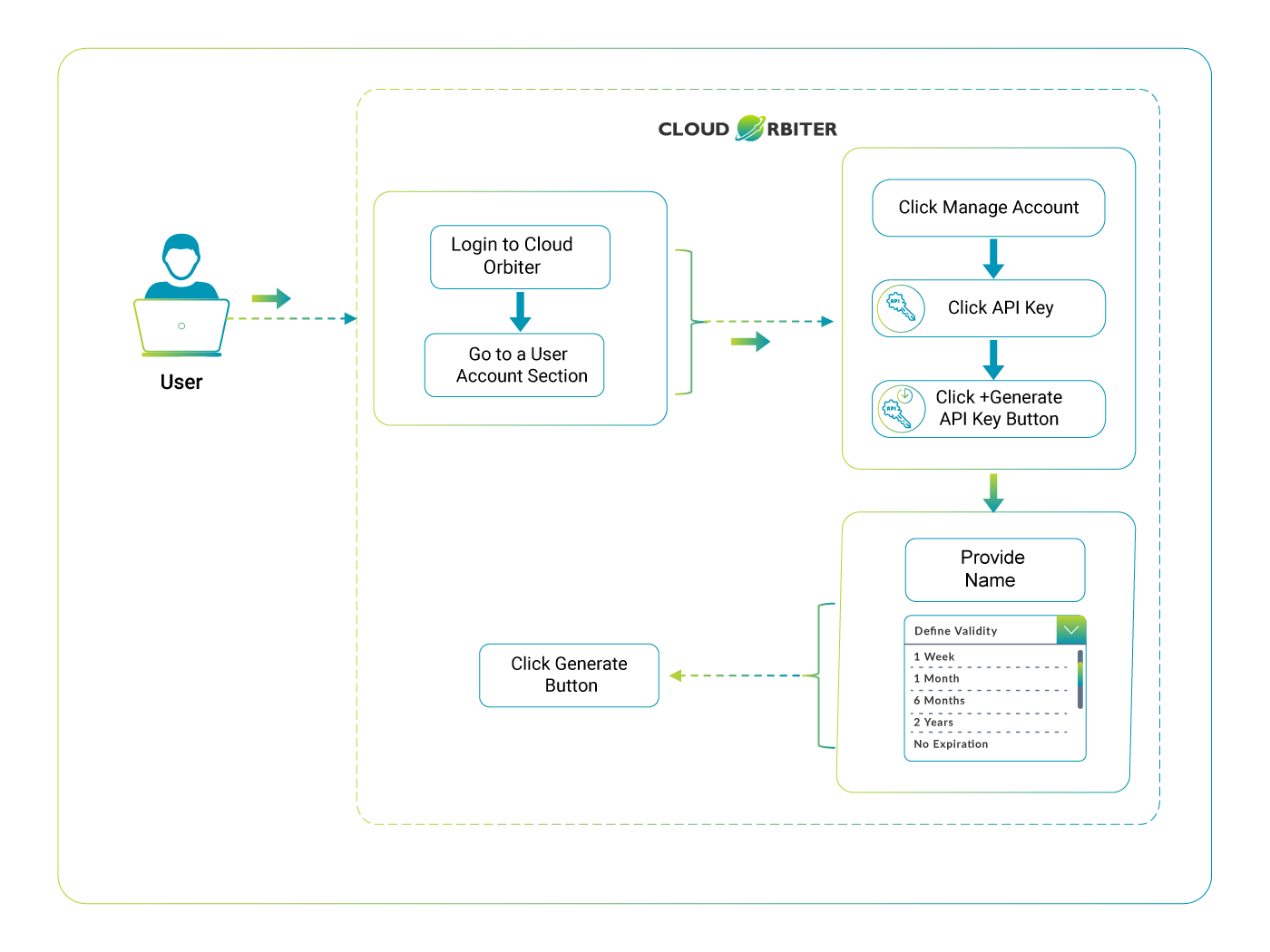
Managing API keys involves several operations that allow you to effectively control access to your API. These operations include creating new keys, listing existing ones, deleting keys, and enabling or disabling them using REST APIs. Currently, this management is user-specific, meaning each user can only view and manage their own API keys.
-
Create API Key: Creating an API key is the process of generating a new key that clients can use to authenticate their requests.
-
List API Keys: Listing API keys allows you to see all the keys that have been created, along with their statuses and permissions.
-
Delete API Key: Deleting an API key removes it from the system, preventing it from being used to authenticate any further requests.
-
Enable API Key: Enabling an API key reactivates it, allowing it to be used for authentication after it has been disabled.
-
Disable API Key: Disabling an API key deactivates it, preventing it from being used to authenticate requests without permanently deleting it.
API Key-Based Authentication
An API key-based authentication is composed of two distinct parts:
Public Key ID: This is used as an identifier for authentication transactions and is expected to be shared as part of the headers in REST API to identify the API key used. Cloud Orbiter's controller ensures this is a unique value per key across the system by using a system-generated unique ID.
Private Secret Key: This is a randomly generated secret corresponding to each key, with a variable length ranging from 35 to 45 characters. This secret key is viewable in the system only once during the creation of an API key. It is then safely stored in the cloud orbiter's controller, and the user device ensures secure communication without sharing the secret key.
API key-based solution introduces a new HTTP Header, "Ce-Auth", which is expected to carry the following value for authentication:
<Public Key ID>.<Expiry TimeStamp>.<HMAC + SHA256 signature>
- The public key ID is a unique key ID used for authentication and plays a crucial role in the process.
- The expiry timestamp defines a token validity. To ensure that the system does not use long expiry tokens, Cloud Orbiter's controller doesn't allow authentication if the specified time is more than five minutes in the future. It also ensures that the token timestamp is not expired.
- The last part of the token is the HMAC signature generated using the SHA256 algorithm where the algorithm takes
<Public Key ID>.<Expiry TimeStamp>as the input data and the secret key corresponding to the API key as the secret for generating the signature.
Security Considerations by Cloud Orbiter
API keys provide a way to secure and control access to APIs. The API secret key is secured with the endpoints after creation, and all authentication is performed using an HMAC signature over the network to ensure a high level of security standards.
- Unique Identifier: Each API key is a unique string that identifies the client making the request. This ensures that each key is tied to a specific user or application.
- Authentication: API keys are used to authenticate the client making the request. Only requests that include a valid API key are processed by the API server.
Flow to Generate API Keys via Cloud Orbiter